As the number of cybercrimes has risen by more than 20 % every year, companies in India would have to show stringent data protection measures...
Read More
Empowering Global Enterprises with GRC Excellence

Global GRC & Compliance Services Across USA, Canada, India & UAE

Build a Resilient Security Framework with ISO 27001, SOC 2 & PCI DSS

Data Privacy Compliance for GDPR & India’s DPDPA

Data Privacy Compliance for GDPR & India’s DPDPA

Data Privacy Compliance for GDPR & India’s DPDPA

A Responsible AI Governance with ISO/IEC 42001
Your Compliance Partners
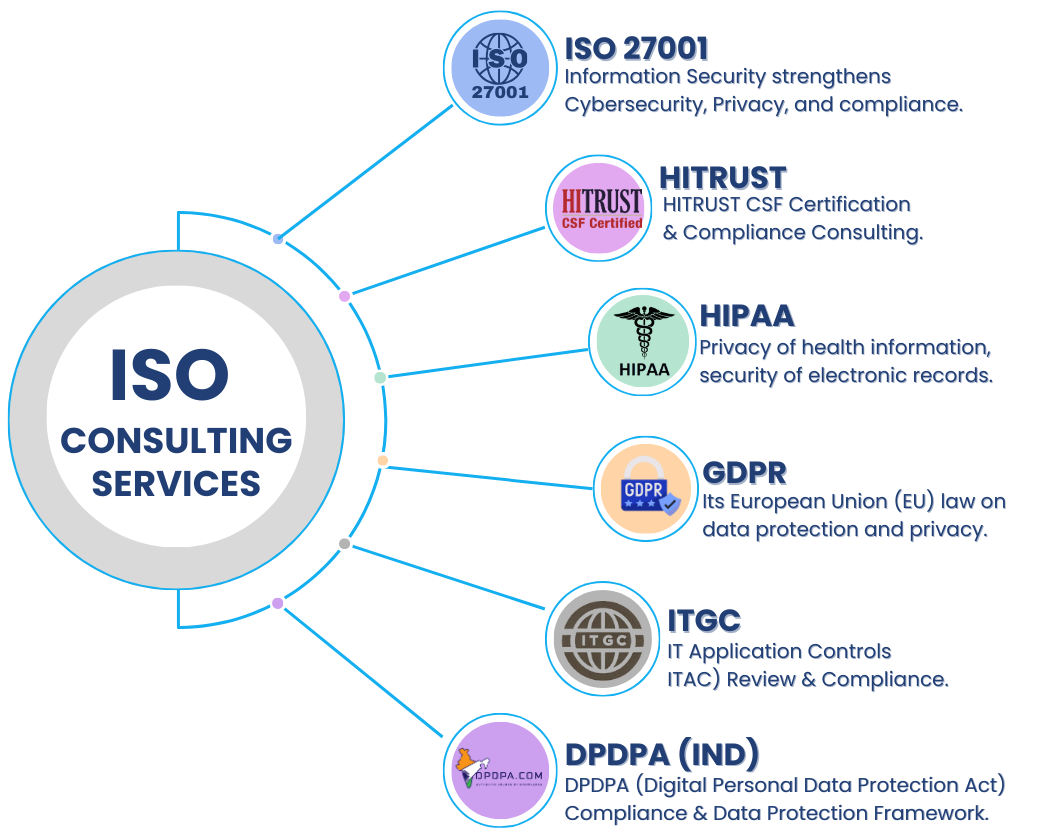
ISO Consulting Services
Experience hassle-free compliance with ISO Consulting Services, a firm dedicated to helping organizations achieve and maintain leading management system standards — including ISO 9001, ISO 27001, SOC 2, PCI DSS 4.0, HIPAA, and compliance frameworks such as HiTrust and NIST. We partner with businesses to strengthen their management systems, enhance productivity and efficiency, safeguard information security, and ensure a safe and compliant workplace environment.
Audit Services

ISO 27001
Information Security enhances Cybersecurity and Privacy Protection through ISMS, ensuring compliance and strengthening your organization’s overall security framework.

SOC 2 (Type I & Type II)
SOC 2 assessment evaluates a service organization’s operational effectiveness and information security controls based on the Trust Services Criteria (TSC).

PCI DSS – 4.0
It is a set of security standards designed to ensure that all companies that accept, process, store, or transmit credit card information maintain a secure environment.

ISO 42001
Matayo guides enterprises in adopting ISO 42001 standards for ethical AI governance, risk assessment, transparency, and accountability in AI systems.

HIPAA
Matayo ensures healthcare organizations maintain HIPAA compliance through PHI protection, risk assessments, and secure health data management.

GDPR
Matayo helps organizations achieve GDPR compliance with data mapping, consent management, and privacy impact assessments across global operations.

DPDPA
Matayo supports organizations in achieving DPDPA compliance with consent-based data processing, privacy governance, and audit automation.

HITRUST
Matayo enables organizations to achieve HITRUST CSF certification with structured risk management, control alignment, and continuous compliance monitoring.

ITGC
Matayo performs ITGC audits to evaluate IT infrastructure, change management, logical access, and operations controls for regulatory compliance and assurance.

ITAC
Matayo helps organizations implement and test IT Application Controls to ensure data accuracy, processing integrity, and audit trail validation within enterprise systems.

Your Cybersecurity Partner
Cyber Security Consultancy Services
Through every service we deliver—from comprehensive risk assessments to adaptive defense strategies—we breathe vitality into the technology that drives your business. Our team of experts and visionaries works alongside you to weave security into the core of your organization, enabling it to thrive with confidence. Here, technology becomes not only a tool, but a trusted guardian that safeguards your journey toward new horizons.
Let us walk with you in building a digital world where safety and ambition move in harmony, where trust in your technology never falters, and where your potential knows no bounds. With Matayo Cyber Security Consultancy Services, the future is not just secure—it’s limitless.

Web Application VAPT
Web Application VAPT identifies and analyzes security vulnerabilities in web applications and websites.

Mobile Application VAPT
Mobile Application (VAPT) is essential for maintaining a high level of security for mobile applications.

API VAPT
Through API VAPT, your data is secured, effectively preventing unauthorized access, data breaches, and potential leaks.

Cloud VAPT
Enhances your cloud security protocols, safeguarding your essential data and applications against potential cyber threats
GET IN TOUCH
Send Your Enquiry
STATISTICS
Our Journey With Clients
We have helped numerous clients achieve compliance with stringent industry standards and regulations, including ISO 27001, GDPR, and PCI DSS.

20+
Clients
Protected

105
VAPT
Applications

55
Audit Services
Consultancy

3 Locations
2 India
1 Canada
Blog
Latest News & Updates
What is ISO/IEC 42001? Understanding the New Global Standard for AI Governance
Artificial intelligence is transforming every industry across the globe. Although AI systems are leading to efficiency and innovation, they are also raising ethical concerns, transparency...
Read MorePCI DSS Compliance Canada: Everything Businesses Need to Know
The safeguarding of customer payment data has become crucial to building client trust and avoiding data breaches in the current digital ecosystem. The Payment Card...
Read More