A Step-by-Step Process for Businesses
In today’s digital landscape, where data breaches and cyber threats are increasingly common, businesses must ensure their data protection mechanisms align with industry standards. For Canadian businesses aiming to enhance trust with clients and partners, SOC 2 Certification in Canada has emerged as a critical framework for ensuring data security, availability, confidentiality, and privacy. In this comprehensive guide, we outline the step-by-step process for achieving SOC 2 certification in Canada, equipping businesses with the knowledge to streamline their compliance journey.
What is SOC 2 Certification?
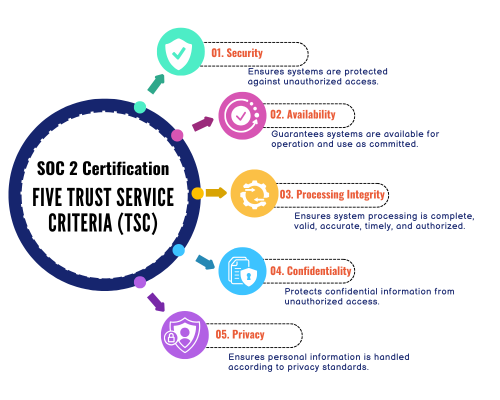
SOC 2 Certification is a compliance standard developed by the American Institute of Certified Public Accountants (AICPA). It focuses on five Trust Service Criteria (TSC):
- Security: Ensures systems are protected against unauthorized access.
- Availability: Guarantees systems are available for operation and use as committed.
- Processing Integrity: Ensures system processing is complete, valid, accurate, timely, and authorized.
- Confidentiality: Protects confidential information from unauthorized access.
- Privacy: Ensures personal information is handled according to privacy standards.
Businesses in Canada aiming for SOC 2 certification can gain a competitive advantage by demonstrating their commitment to safeguarding sensitive data and meeting regulatory compliance requirements.
Why SOC 2 Certification is Essential for Canadian Businesses
SOC 2 Certification in Canada is particularly relevant for businesses handling sensitive customer data, such as SaaS providers, cloud service providers, and IT organizations. Key benefits include:
- Building Customer Trust: Ensures customers their data is secure and protected.
- Regulatory Compliance: Helps businesses meet provincial and federal data protection laws, such as PIPEDA (Personal Information Protection and Electronic Documents Act).
- Competitive Edge: Establishes your organization as a trusted partner for global clients.
- Risk Mitigation: Identifies and addresses vulnerabilities in your systems and processes.

Step-by-Step Process to Achieve SOC 2 Certification in Canada
1. Understand the SOC 2 Requirements
Begin by familiarizing yourself with the Trust Service Criteria and their applicability to your business processes. Canadian businesses must align SOC 2 requirements with relevant data privacy laws like PIPEDA.
2. Define the Scope of Certification
To ensure an effective audit process, define the scope of your SOC 2 certification. This includes:
- Identifying systems, applications, and processes to be included.
- Determining applicable Trust Service Criteria based on customer needs.
- Aligning the scope with your organization’s risk management strategy.
3. Conduct a Gap Analysis
A gap analysis helps identify discrepancies between your current security posture and SOC 2 requirements. Key steps include:
- Reviewing existing controls and policies.
- Identifying gaps in security, availability, confidentiality, or privacy measures.
- Prioritizing areas needing improvement.
4. Implement Required Controls
Based on the gap analysis, implement necessary technical and operational controls. Some essential controls include:
- Access Controls: Ensure role-based access to sensitive data.
- Encryption: Secure data in transit and at rest.
- Monitoring Systems: Deploy monitoring tools to detect unauthorized access or anomalies.
- Incident Response Plan: Create a clear plan for addressing security incidents.
5. Prepare Documentation
Comprehensive documentation is crucial for SOC 2 certification. This includes:
- Security policies and procedures.
- Risk assessment reports.
- Incident management records.
- Evidence of control implementation.
Proper documentation not only supports the audit process but also enhances internal awareness of security protocols.
6. Engage a Certified SOC 2 Auditor
Select an accredited CPA (Certified Public Accountant) firm with expertise in SOC 2 audits for Canadian businesses. Ensure the auditor is familiar with regional data privacy laws and regulations.
7. Perform a Readiness Assessment
Before the formal audit, conduct a readiness assessment. This involves:
- Reviewing implemented controls.
- Identifying potential gaps or weaknesses.
- Addressing any issues before the audit begins.
8. Undergo the SOC 2 Audit
The audit process consists of two main types:
- Type 1 Audit: Evaluates the design of controls at a specific point in time.
- Type 2 Audit: Assesses the operating effectiveness of controls over a period (usually 6-12 months).
When deciding between the two, consider:
- Choose SOC 2 Type 1 if you’re new to SOC 2 compliance and want a quicker validation of control design.
- Opt for SOC 2 Type 2 if you need to demonstrate sustained control effectiveness over time for critical clients or contracts.
During the audit, the auditor will:
- Review evidence supporting control implementation.
- Test the operating effectiveness of controls.
- Document findings and provide a detailed audit report.
9. Review the Audit Report
The audit report highlights your compliance status, control effectiveness, and any areas needing improvement. Use this report to:
- Address identified issues.
- Share results with clients and stakeholders.
- Strengthen internal security measures.
10. Maintain Continuous Compliance
SOC 2 compliance is an ongoing process. To maintain certification:
- Regularly update security controls.
- Conduct periodic internal audits.
- Train employees on SOC 2 policies and practices.
Challenges in SOC 2 Certification and How to Overcome Them
Achieving SOC 2 certification in Canada can be complex. Common challenges include:
- Resource Constraints: Address by allocating dedicated personnel for compliance activities.
- Understanding Requirements: Seek guidance from SOC 2 consultants or experts.
- Integration with Existing Processes: Use automation tools to streamline compliance workflows.

Conclusion
SOC 2 Certification in Canada is an essential milestone for businesses aiming to demonstrate their commitment to data security and privacy. By following the step-by-step process outlined above, organizations can not only achieve compliance but also build trust with clients, strengthen their market position, and mitigate risks effectively.
When deciding between SOC 2 Type 1 and Type 2, consider your business’s current maturity and the expectations of your clients. Type 1 audits are suitable for validating initial control designs, while Type 2 audits are essential for demonstrating operational consistency over time.
At Matayo, we specialize in guiding Canadian businesses through their SOC 2 certification journey. From readiness assessments to implementing controls and undergoing audits, our team ensures a seamless process tailored to your organization’s needs. Let us help you build trust, achieve compliance, and secure your data with confidence.
About the Author:
G. Sudhakar: As the CEO of Matayo AI Solutions Pvt. Ltd., G. Sudhakar brings over two decades of experience in IT, cybersecurity, and compliance. Under his leadership, Matayo has become a trusted name in providing innovative and effective GRC solutions. With a strong vision for empowering businesses, he ensures every client achieves their compliance goals efficiently.

