In an era where data security and trust equate to business success, businesses must be perceived as having sound processes in place for protecting information. One of the most recognized methods of accomplishing this is by obtaining SOC 2 Type 1 Certification. It attests that a business has established and documented solid internal controls for handling its data securely at a point in time. Whether you are a cloud service provider, a SaaS business, or just an enterprise with data, you need to know about the SOC 2 Type 1 Audit, the report, and the SOC 2 Type 1 Compliance process. We are going to walk you through it step by step.
Understanding SOC 2 Type 1
To truly understand what SOC 2 Type 1 is, it’s best to begin by considering the overarching structure into which it falls, the SOC reporting system released by the American Institute of Certified Public Accountants (AICPA). The framework was created in an effort to help service organizations demonstrate that they secure customer information and process it correctly. This is where SOC 2, and more precisely the emphasis on non-financial reporting in respect of this security, availability, processing integrity, confidentiality, and privacy, comes in. This standard has gained traction, particularly among technology and cloud-based companies holding sensitive customer information. This is the beginning of the remainder of the series.

What is SOC 2?
SOC 2, or System and Organization Controls 2, is a set of security principles that have been defined by the American Institute of Certified Public Accountants (AICPA). It is meant for organizations that hold, process, or handle customer information. SOC 2 proves that a business has proper security practices and policies.
It comprises five Trust Services Criteria:
- Security (mandatory)
- Availability
- Processing Integrity
- Confidentiality
- Privacy
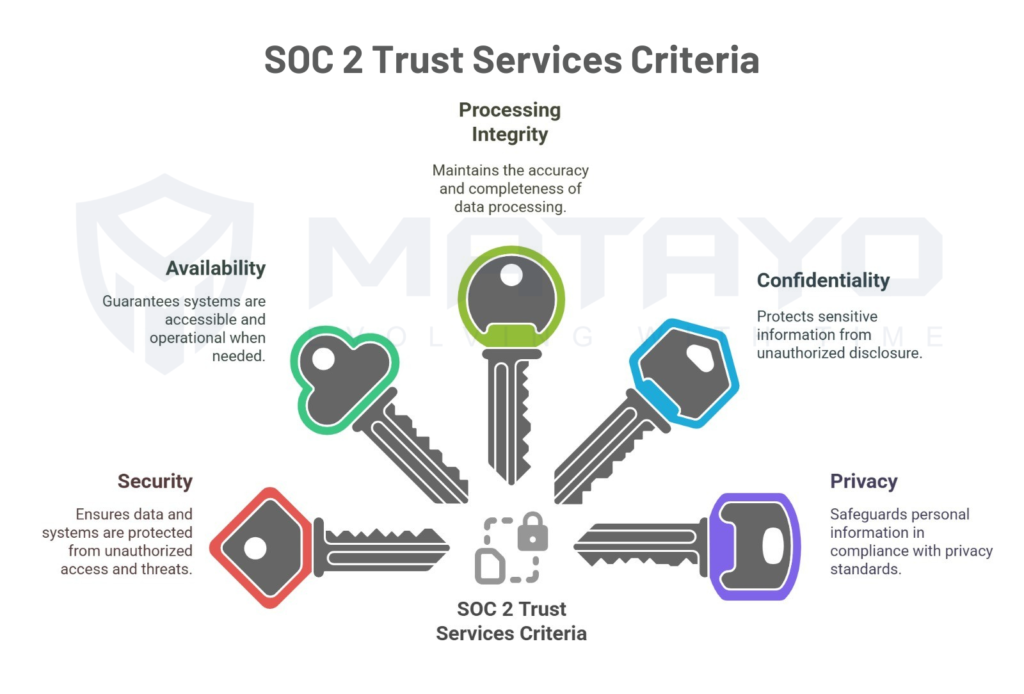
Each organization can decide which of the above criteria apply. However, security is always one. The goal is to establish customers’ trust by proving that the organization has the capability of protecting information. SaaS, cloud, and IT service providers, in any industry, especially if there’s sensitive data involved, are making SOC 2 the go-to framework.
What Does “Type 1” Mean?
Under an audit, businesses are tested against SOC 2 Type 1 to ensure that they have designed internal controls as planned from a specific date. The audit tests whether the processes and systems are in existence, but not whether they operate well in the long term.
This is different from SOC 2 Type 2, where the operating effectiveness of those controls is being assessed over a longer duration, generally over 3 to 12 months. SOC 2 Type 1 is an excellent means of opening doors and usually serves as a bridge to the far more comprehensive Type 2 audit. It puts into action the preparedness of clients and regulators for a business.
SOC 2 Type 1: Why Organizations Opt for It
Most organizations, especially new companies or startups, begin with SOC 2 Type 1 Certification. It will be quicker and use fewer resources compared to Type 2. However, it is best for:
- Compliance with customer and vendor demands.
- Establishing trust and credibility.
- Preparation for future SOC 2 Type 1 Compliance or a Type 2 audit.
Completing a SOC 2 Type 1 audit is an indicator that an organization takes security seriously and has a solid foundation. This attestation is frequently essential for companies that are building B2B relationships. In addition to that, having the SOC 2 Type 1 Report available may be a deal breaker when it comes to raising capital, pitching a sale, and negotiating a transaction.

SOC 2 Type 1 Certification
So, what is SOC 2 Type 1 Certification, who can provide it, and what are the steps involved?
Is SOC 2 Type 1 a “Certification”?
Technically speaking, SOC 2 Type 1 Certification is not actually a certification. It is a report and a document from an independent, licensed CPA (Certified Public Accountant) of an AICPA-approved firm.
The auditor gives an opinion that your firm has implemented adequate controls as of a specific date. Technically, it’s not a “certification,” but the device industry refers to it as such all the time.
Who can give a SOC 2 Type 1 Report?
Only CS/CM licensed CPA firms or licensed audit firms can issue a SOC 2 Type 1 Report. The practices must have IT infrastructure auditing experience, cloud services experience, data privacy experience, and internal control environment experience.
Auditors add the third-party seal of approval, confirming that the company’s processes are in place to enable the selected Trust Services Criteria. They create the final report after they have reviewed the documentation and interviewed team members.
Timeline and Readiness for Certification
It usually takes anywhere from 6 – 10 weeks to become SOC 2 Type 1 compliant, depending on how prepared you already are. Here is what the process entails:
- Scoping: The clients should know what we are including and all the other minor details.
- Assessment: Identify deficiency areas or where you fall short.
- Remediation: Repair what’s been identified.
- Audit Fieldwork: Document and respond to audit questions.
- Final Report: Receive your SOC 2 Type 1 Report.
Companies that plan, especially those that use consultants, can navigate the process rather easily.
SOC 2 Type 1 Audit Process
At the heart of the SOC 2 Type 1 Certification is the SOC 2 Type 1 Audit. Preparation is everything. Your organization must scope the audit, determine which controls have internal owners, and get documentation. This would include:
- Security policies
- Access control procedures
- Risk assessments
- Incident response plans
- Vendor management practices
Such preparation reduces back-and-forth with auditors and makes the process smoother.
Gap Analysis and Remediation
Prior to being audited for reauthorization, most companies do a gap analysis, either in-house or via a consultant. The objective is to determine:
- Missing or out-of-date policies
- Weak password policies
- No logging or monitoring
- Subpar vendor risk management
After you identify those gaps, your team sets about remedying them, i.e., you repair what’s broken or missing.
The Actual Audit
During the audit, the CPA or auditing firm should:
- Evaluate your system and organizational controls
- Compare received practices with stated policy
- Interview employees for clarification
- Request Screenshots, Logs, and Other Evidence
There are two forms of SOC 2 Audit: Type 1 and Type 2. The SOC 2 Type 1 Audit is a one-point-in-time audit that focuses on the design of controls, as opposed to the operating effectiveness of these controls for months. That makes the process less intrusive than the Type 2 audit, which measures the effectiveness of controls over months.
Auditor’s Report and Deliverables
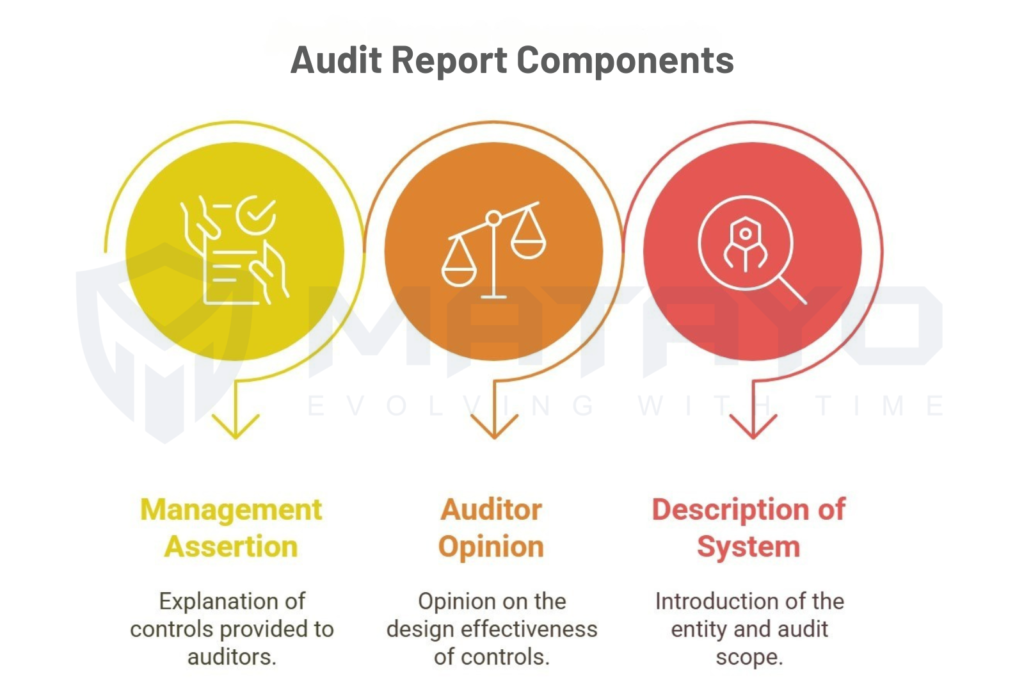
And when everything goes perfectly, you’ll receive your SOC 2 Type 1 Report, which includes:
- Management Assertion: You explain to us a description of controls.
- Auditor Opinion (AO): Their opinion on whether or not your controls are well designed.
- Description of System: Well, the only thing they can describe is to provide an introduction of your entity and the scope of your audit.
Share your SOC 2 Type 1 Report with customers and business partners to demonstrate compliance.
SOC 2 Type 1 Compliance
It’s not done when you pass the audit. And with SOC 2 Type 1 Compliance comes continuous responsibility. Your team must continue to do so as specified in your report and be ready for future exams.
What is Compliance in SOC 2 Type 1?
In order to be SOC 2 Type 1 Compliant, you will require:
- A clearly defined set of systems in scope for the audit
- Basis for Opinion: A quality control system that adheres to the selected Trust Services Criteria
- Documentation supporting each control
It also includes being prepared to answer customers or regulators with additional questions. Being in compliance is a natural result when you incorporate security into your everyday life.
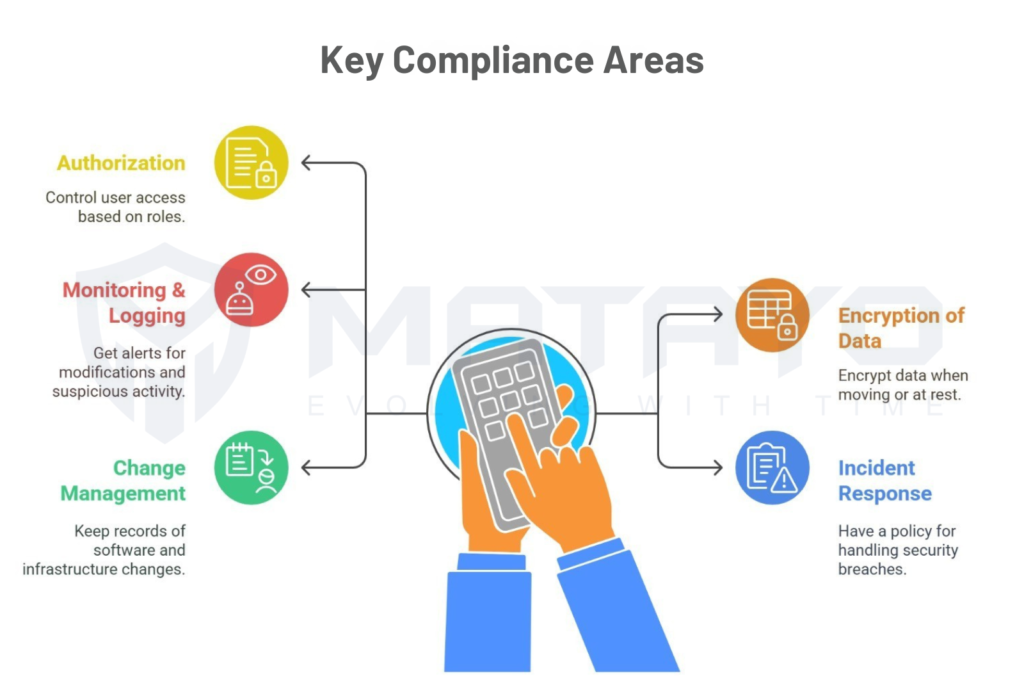
Key Compliance Areas
To remain SOC 2 Type 1 compliant within your organisation, focus on:
- Authorization: Control access to users based on roles and responsibilities.
- Encryption of Data: Encrypt data in transit and at rest using strong encryption.
- Monitoring & Logging: Alerts on modifications and warning signs of suspicious activity.
- Incident Response: You must have a policy for handling breaches.
- Change Management: Keep records of software and infrastructure changes.
Regular internal audits and training of teams all contribute to having these regions robust and consistent.
Internal Ownership & Responsibility
Compliance and security are no longer the sole domain of one team. Various departments must work together:
- IT & Engineering: Manage system-level logging & control.
- HR: Manage onboarding, offboarding, and staffing access.
- Legal: Keep an eye on your contract risks and obligations.
- Executives: Implement a culture of accountability and fund those compliance initiatives.
Clear ownership results in better SOC 2 Type 1 Compliance as well as successful future audits.
How Matayo Can Help You Achieve SOC 2 Type 1 Report in 5 Steps?
Here’s how Matayo leads you on the journey to SOC 2 Type 1 with a precise and systematic approach:
- Scope of Definition: We assist you in identifying exactly what systems and processes will fall under your audit.
- Gap Analysis: We find missing or deficient controls so you don’t have to guess what to fix.
- Remediation Assistance: We guide you in your efforts to fix gaps and provide thorough guidance during the process.
- Audit Ready: Everything we deliver to you is audit ready.
- Audit help: We will be with you every step of the way during the Audit, providing answers and helping you to receive your SOC 2 Type 1 Report.
With Matayo SOC 2 Type 1 Compliance is easier, faster, and stress free.
Conclusion
There is more to SOC 2 Type 1 than just checking the box. It’s a badge for your clients, co-founders, and investors that you care about defending data. If your organization is just getting started or you’re building security maturity for the long term, a SOC 2 Type 1 certification, audit, and compliance set a solid foundation.
Matayo assists rapidly growing companies along their journey to SOC 2 Type 1 Certification. Hire Matayo from readiness through report so your audit is stress-free, rapid, and successful.

FAQs
The SOC 2 Type 1 examines internal controls at one point of time, whereas SOC 2 Type 2 measures the effectiveness of those controls over a duration, typically 3-12 months. Type 1 is a good place to start, particularly for early-stage companies.
Generally, it takes 6 to 10 weeks for organizations to complete the SOC 2 Type 1 process, depending on how prepared they are, the documentation that is already in place, and the remediation that is needed. By working with a consulting partner, such as Matayo, this timeline can be significantly trimmed.
The SOC 2 Type 1 is not a legal requirement but is commonly required by enterprise customers, investors, and partners, particularly for B2B SaaS companies that handle sensitive customer data. It builds trust and satisfies vendor risk requirements.
An SOC 2 Type 1 Report can only be issued by an independent CPA or licensed audit firm approved by the AICPA. The company should be experienced in IT audits, cloud infrastructure, and data security.
You’ll need to provide clear documentation around security policies, access control and password rules, incident response procedures, risk management practices, and vendor risk assessment processes to the auditor to assess the design of your internal controls.
SOC 2 Type 1 Certification is an ongoing process, not a one-time event. Your company must:
- Continue following documented policies
- Maintain access controls and logs
- Conduct regular internal audits
- Prepare for future SOC 2 Type 2 audits
- Assign clear internal ownership across departments (IT, HR, Legal, etc.)

