In a digital-first world, protecting user data isn’t just good practice, it’s non-negotiable. With new threats constantly appearing and increasing regulatory scrutiny on data, companies want to show that their ability to protect data is a fact, not just a service. This is where the SOC 2 Type 2 Certification comes to the rescue.
SOC 2 Type 2 is an extremely valued compliance standard that demonstrates your systems are secure and your internal controls are working as they should, consistently and without fail, over time. If you’re a SaaS company, cloud infrastructure company, or data-driven platform, SOC 2 Type 2 allows you to build trust, acquire enterprise customers, and grow with confidence.
In this in-depth tutorial, we’ll walk you through the SOC 2 Type 2 Audit, certification, and how to handle your end report.
What is SOC 2 Type 2 Certification?
SOC 2 Type 2 is a framework developed by the American Institute of Certified Public Accountants (AICPA). It evaluates how effectively your business safeguards customer data, not a snapshot in time, but across a monitoring period typically 3, 6, or 12 months. That’s what distinguishes SOC 2 Type 2 from SOC 2 Type 1, which is really just a snapshot check to see if systems and policies are installed at some moment in time. Type 2 shows instead that your organization can keep running those controls against real-world situations.
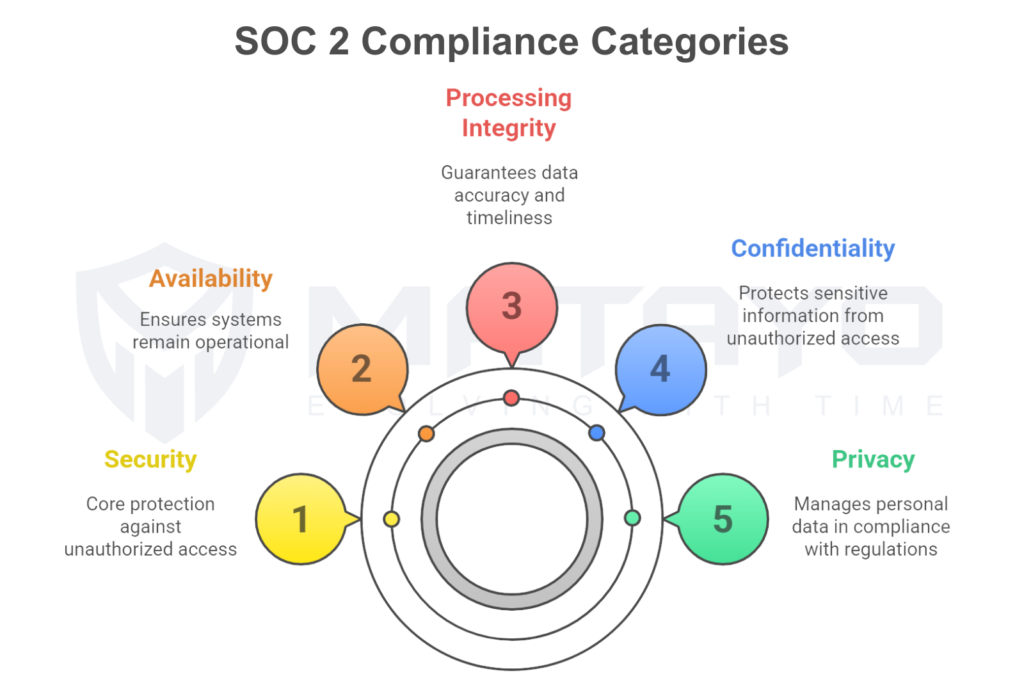
SOC 2 Type 2 corresponds to the Trust Services Criteria (TSC) and encompasses:
Security (Mandatory)
This is the heart of SOC 2, and it’s used for all of the audits. It gives security to your systems against unauthorized access and attacks. Firewalls, anti-malware software, MFA user access reviews, and incident response plans are controls in this category.
Availability
This ensures that your systems remain up and running. It has controls for monitors for performance and disaster recovery, as well as failover and capacity controls.
Processing Integrity
That way, your systems can capture and process all your data in its entirety and in a timely manner. Such controls include workflow testing, transaction validation, and integrity checking.
Confidentiality
This will ensure sensitive business or client information is not accessed by anyone without authorization. Possibilities for controls include encryption, secure data storage, role-based access, and NDAs.
Privacy
The privacy concept is built around the use of personally identifiable information (PII). It has data collection and user consent policies, secure storage and sharing, and deletion policies according to GDPR and CCPA.
Any one or more of the five TSCs may not be needed, so the client can choose any criteria that are applicable to them, though Security is mandatory for all.

Why SOC 2 Type 2 Matters?
Well, that’s because SOC 2 Type 2 is not merely a seal of approval; it’s a strategic tool. It indicates to your stakeholders that you don’t merely talk about safeguarding data, you’re actually implementing it, day in and day out.
This is especially vital if you are handling client data, monetary details, or log-ins from users. More and more of your prospective customers will anticipate that you possess SOC 2 Type 2 and won’t do business with you if they’re not convinced you do. It’s normal now in vendor audits and due diligence audits in most sectors.
Some of the most frequent industries that require SOC 2 Type 2:
- SaaS businesses (particularly enterprise-oriented)
- Cloud providers
- Managed service providers (MSPs)
- Fintech and Healthtech platforms
- HR and Martech solutions
- Early-stage startups pursuing big clients or investors
And even if it’s not required in your market, attaining SOC 2 Type 2 proves trustworthiness, scalability, and maturity, all qualities that you’d desire clients, partners, and investors to have respect for and from you.
The SOC 2 Type 2 process
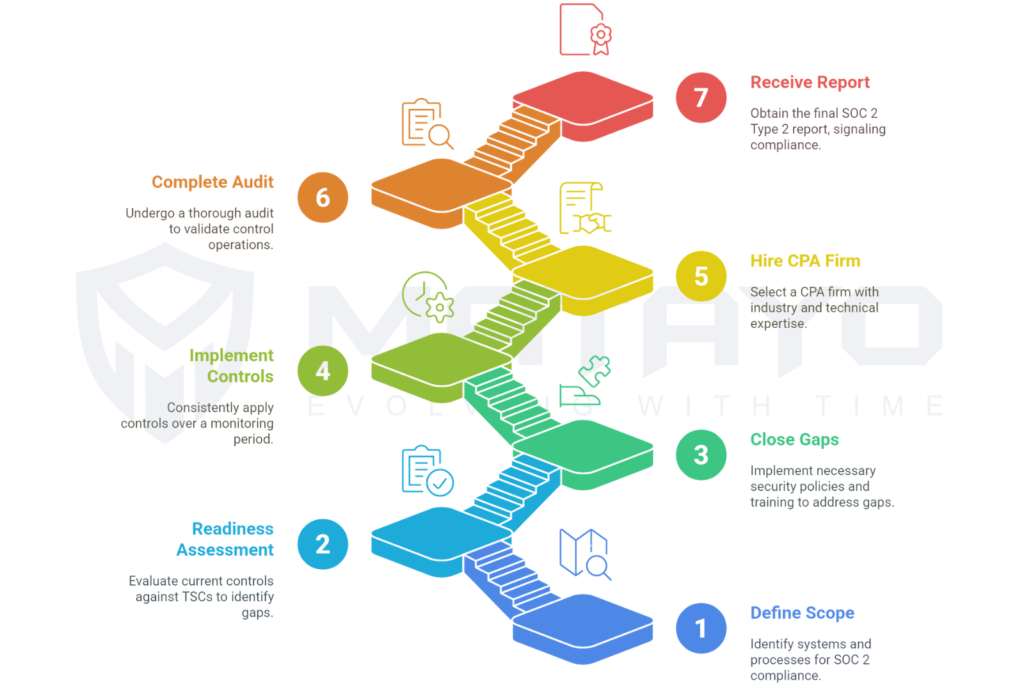
Having a SOC 2 Type 2 Certification takes a long time, and to become SOC 2 Type 2 Certified, extensive steps and months of planning are involved. Here’s how to do it:
Step 1: Define the Scope
Understand what subsystems, departments, and processes are within scope for SOC 2. A targeted, specific approach makes this manageable, such as customer-facing applications, core infrastructure, storage backends, and third-party systems.
Step 2: Perform a Readiness Assessment
Before you hire an auditor, have them check your controls against the TSCs. That’s a readiness assessment. It will give you a sense of where gaps and non-compliance issues exist. Many companies hire consultants or use compliance automation platforms, such as Vanta, Drata, Secureframe, etc., for this step alone.
Step 3: Close Gaps
You’ll have to plug holes, based on your findings. It could be writing security policies, establishing encryption, building audit logs, or training staff. This step is key to a successful real audit.
Step 4: Implement Controls and Start Monitoring
When you implement these controls in practice on a day-to-day basis, they need to be implemented consistently over your chosen time frame. This might be 3, 6, or 12 months. This is when you record and adhere to all aspects, from access logs to backup routines.
This ongoing monitoring is the core of SOC 2 Type 2. It shows that your processes are compliant on the page and they operate as they should in practice.
Step 5: Hire a CPA ( Certified Public Accountant ) Firm
Only a CPA or a CPA firm can audit. Choose one who understands your industry and technical stack. They will review your documentation, interview your employees, and validate the stability of control operations during the monitoring time frame.
Step 6: Complete the SOC 2 Type 2 Audit
The auditor then obtains the evidence necessary to justify the above statement through fieldwork. They’ll examine access management logs, test your encryption protocols, review your incident response plans, and so on. Just be sure to confirm every control was properly functioning while monitoring.
Step 7: Receive the Final Report
If you pass, your CPA firm issues you a SOC 2 Type 2 Report with a formal assertion of compliance. And that is a trust signal that you can send to your customers, your prospects, and your partners.
What Happens During an SOC 2 Audit?
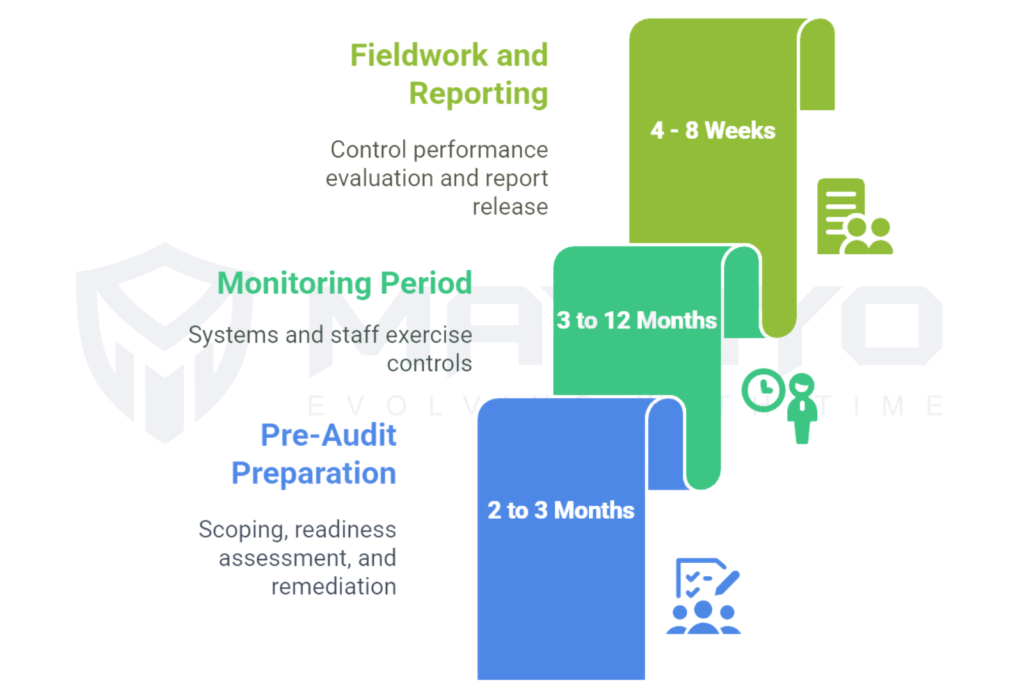
The SOC 2 audit procedure has three main stages:
Pre-Audit Preparation (2–3 months)
This includes scoping, readiness assessment, and remediation.
Monitoring Period (3–12 months)
Systems and staff must still exercise controls throughout this time. It is not sufficient to possess policies; each policy must be substantiated.
Fieldwork and Reporting (4–8 weeks)
When the monitoring period completes, your control performance is evaluated by the CPA firm, and your report is subsequently released.
What Do Auditors Look For?
Auditors will review:
- Access Controls: Role-based permission? Are regular access reviews being done?
- Change Control: Are updates to applications tested and approved prior to deployment?
- Encryption: Are your data encrypted while being stored and in transit?
- Incident Handling: Are incidents being properly logged, escalated, and resolved?
- Vendor Risk: Do you conduct third-party tool and service evaluations?
They will request logs, policies, onboarding documentation, evidence that employees were trained, and process documentation. They may also interview to ensure that the team’s understanding.
Common Pitfalls And How to Avoid Them
While taking SOC 2 type 2 certification, listed below are a few common pitfalls that should be avoided:
Insufficient Documentation
Monitor access logs, audit trails, and changes with automated solutions. Write it all down.
Lack of Consistency
Automate routine tasks like backups, testing, and patching. Clearly define ownership.
Employee Unawareness
Educate them on what SOC 2 is and what they will be asked to do for the audit.
Overly Broad Scope
Don’t let your scope get too big. Narrow your scope to critical systems and processes.

SOC 2 Type 2 Report: Structure & Use Cases
Your SOC 2 Type 2 Report is more than a certificate; it’s a trust signal that builds trust and legitimacy. The final SOC 2 Type 2 Report you get includes:
- Management Statement: Assurance by your company on what it is performing for parties in control.
- Auditor’s Opinion: An opinion by an external CPA on the effectiveness of your controls.
- System Description: What your technology stack is, what the process is, and what services you provide.
- Test Results—Alternative: A more detailed presentation from both control sides during the test time period.
This is not just a momentary deliverable; it’s your market credibility card. Shorten sales cycles, eliminate procurement friction, and enhance your stance in security reviews.
How Is It Used?
Win enterprise customers: SOC 2 Type 2 proves you can be trusted with customers’ sensitive information
- Accelerate vendor evaluations: Fewer security questionnaires and more client retention.
- Build your brand: Foster a reputation of operational strength.
- Scale facilitation: Facilitate scale access to investors’ trust and partnership prospects.
- Strengthen security posture: Establish an enduring sense of internal discipline and awareness.
Conclusion
SOC 2 Type 2 Certification is concrete proof that your business is not only lip-serving information security but is living it day after day. From scoping and remediating vulnerabilities to getting through the final audit, each step of the way is a chance to build credibility and strength.
Whether you’re trying to attract enterprise clients, simplify procurement, or just develop a strong internal security posture, SOC 2 Type 2 is the mountain peak. Matayo is here to help you every step of the way. Ready to begin your journey? Contact Matayo today, and their expert consultations and guidance will ease your journey along the way.

FAQs
SOC 2 Type 2 is widely trusted because it proves your security controls are not only in place but also consistently operating over time. Unlike certifications that only assess documentation or one-time controls (like ISO 27001 or SOC 2 Type 1), Type 2 evaluates real-world effectiveness across months, making it highly credible for enterprise customers and due diligence teams.
The entire SOC 2 Type 2 process generally spans 6 to 12 months and includes the following:
- Pre-audit preparation and remediation (2–3 months)
- Monitoring period (3–12 months)
- Data collection and report writing (4 to 8 weeks)
However, the timeline can be dramatically decreased with proper planning and experienced guidance from Matayo.
SOC 2 Type 2 is critical for SaaS providers, cloud platforms, fintech, healthtech, MSPs, HR tech, and martech firms, particularly those processing customer data and serving enterprise clients. Even early-stage startups with a focus on scaling desire to achieve this certification, as it’s what many of their vendor risk requirements call for, and it gains trust.
Yes. You can customize the scope to fit your business. Security is said to be required, but the others (Availability, Processing Integrity, Confidentiality, and Privacy) are optional depending on the situation. Generally, most SaaS companies take security, availability, and confidentiality as the base case.
While undergoing a SOC 2 Type 2 audit, auditors usually request:
- Access control logs
- Change management documentation
- Encryption protocols
- Security awareness training records
- Incident response logs
- Third-party/vendor assessments
- Policy texts and evidence of their operationalization
Auditors could also talk to employees to confirm comprehension and implementation of the policy.
SOC 2 Type 2 compliance is a continuous journey. The report is current for 12 months after the monitoring period ends, so the companies need to have annual audits in order to keep their reports current and to show that they remain effective during that period of time.
To truly understand what SOC 2 Type 1 is, it’s best to begin by considering the overarching structure into which it falls, the SOC reporting system released by the American Institute of Certified Public Accountants (AICPA). The framework was created in an effort to help service organizations demonstrate that they secure customer information and process it correctly.

