ISO 27001 Services
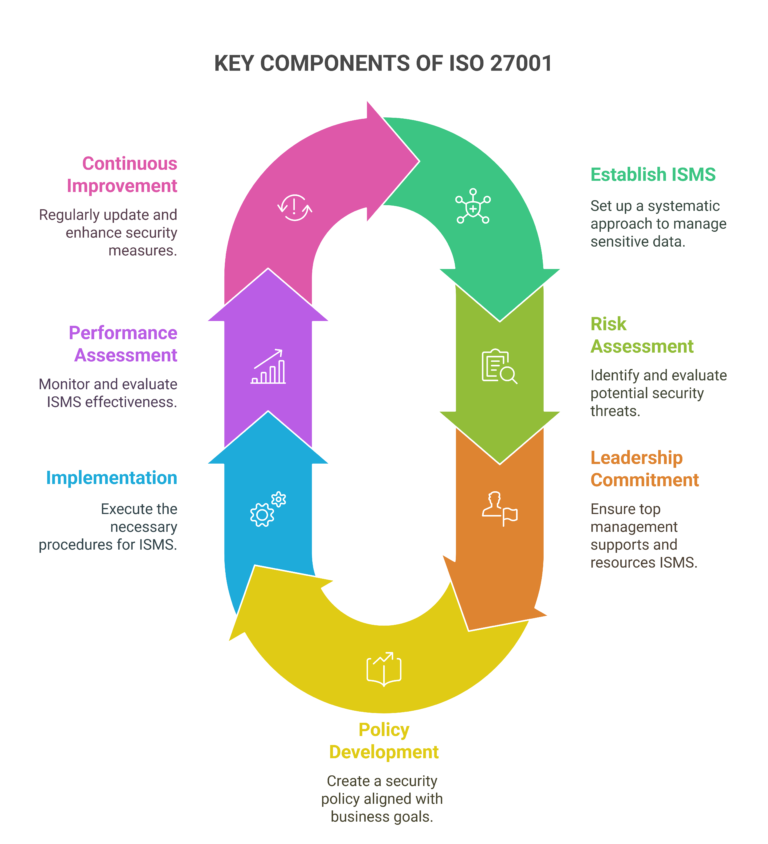
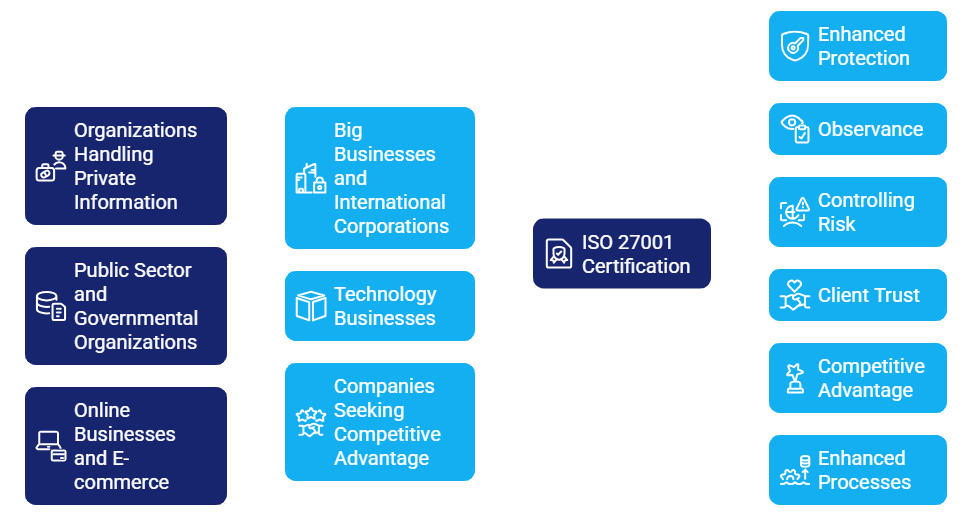
ISO 27001 is a standard widely recognized internationally for managing information security, drafted by the International Electrotechnical Commission (IEC) and International Organization for Standardization (ISO). It gives a systematic approach to protect sensitive data. Through the use of a risk management process, the standard addresses individuals, procedures, and IT systems.