SOC 2 (Type I & Type II) Services
Matayo helps businesses to successfully maneuver the SOC 2 process, by corroborating they meet industry standards for security, availability, processing integrity, confidentiality, and privacy.

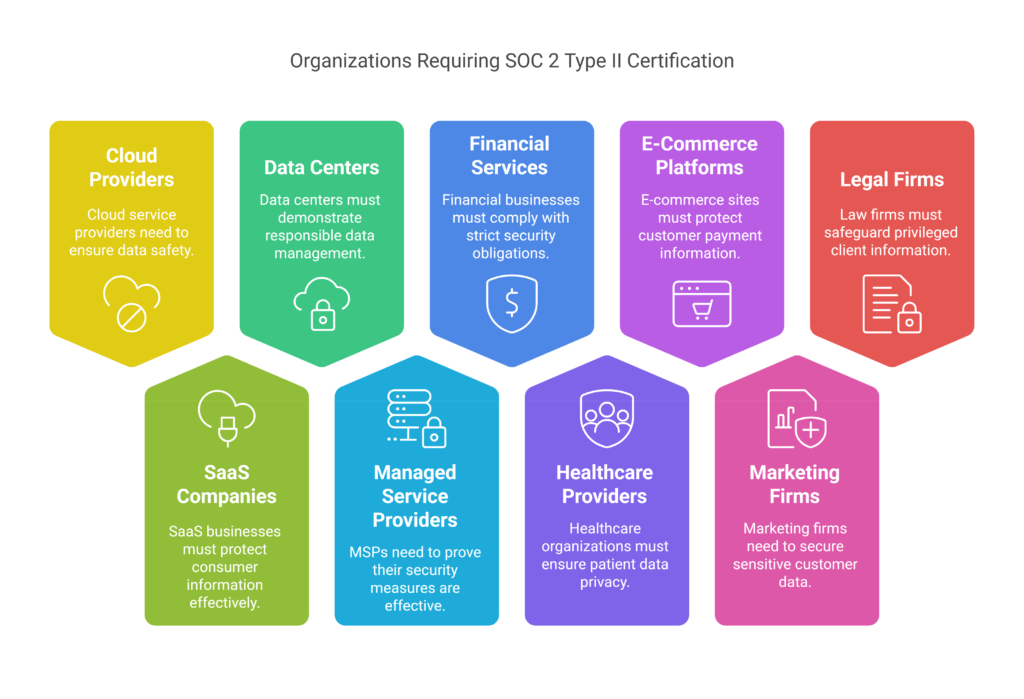
SOC 2 (Type I & Type II) Services: Ensuring Trust and Transparency in Data Security
In case your organization has sensitive customer information, showing that you take security seriously is not a nice-to-have, but rather a prerequisite. Matayo’s SOC 2 services provide comprehensive support towards meeting these demands and instilling faith in your clients and stakeholders.