Canadian businesses that handle customer-sensitive data must follow exact security protocols and operational standards to build integrity with their clients, with simultaneous protection measures in place for the data. Organizations in Canada use SOC 2 Certification as their recognized framework for enforcing strong security controls and proving their commitment to defend customer information securely.
Organizations in cloud computing, accounting, medical and tech sectors must obtain SOC 2 certification because data security is their primary focus. The guide details SOC 2 Certification in Canada by presenting information about its significance, certification procedures, and typical business obstacles during standard compliance assessment.
Understanding SOC 2 Certification in Canada
The SOC 2 Certification in Canada is a security framework that enables businesses to defend customer information while meeting the industry’s best standards. The certification framework comes with five Trust Services Criteria: Security, Availability, Processing Integrity, Confidentiality, and Privacy. Having a SOC 2 certification is a must-have for those businesses that manage cloud-based or third-party data services. Companies can easily choose between SOC 2 Type I and SOC 2 Type II certifications based on their assessment needs. Type I provides the single-time evaluation of controls at a target date, while Type II examines control effectiveness throughout a duration. Businesses must pass a SOC 2 audit by an unaffiliated firm to receive certification that demonstrates their security principles compliance through a detailed report.

The Importance of SOC 2 Certification in Canada
Modern businesses that manage customer information must enforce robust security protocols because of intensifying cyber dangers and intensified data protection standards. Implementing a solid security system protects businesses from possible threats by reducing data breach occurrences and following industry guidelines. Organizations that prove their dedication to safeguarding private data become more competitive due to security and trust becoming fundamental aspects of business partnership development. A security program designed well protects organizations from enduring expensive legal implications and financial consequences that result from carelessness in safeguarding data.
Security certifications that provide recognition strengthen trustworthiness while creating reassurance for customers along with business partners and stakeholders about implemented safekeeping procedures. Organizations within cloud computing, finance, and healthcare need proof of security compliance as an initial step before partner relations start. Security certification recognition helps organizations fulfil their contractual requirements and simplifies the process of future verification of SOC 2 Compliance Canada. Businesses can improve their market position and build client trust through thorough control implementation and independent audit procedures.
Steps to Achieve SOC 2 Certification in Canada
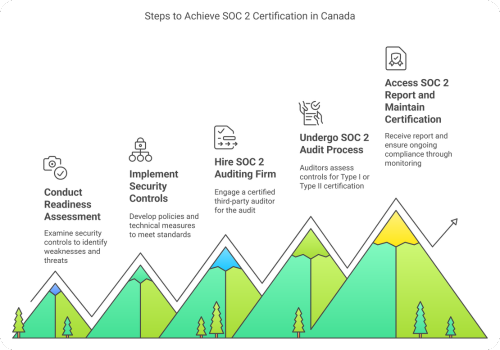
A methodical method is needed for security certification because it establishes every essential control requirement. Businesses must follow five to six key steps, from a security framework assessment and proceed to independent audit completion. The following breakdown provides a necessary guide for completing security certification steps.
1. Conduct a Readiness Assessment
Businesses must examine their security controls before initiating SOC 2 certification procedures. A readiness assessment serves multiple purposes by discovering weak areas and assessing potential threats as well as determining which improvements are needed to fulfill Trust Services Criteria standards.
2. Implement Security Controls
Organisations need to create procedures together with policies along with technical protective measures because they need to match the SOC 2 standards. The operational security depends on implementing access controls as well as data encryption technology together with monitoring systems and incident response plans.
3. Hire a SOC 2 Auditing Firm
Only a certified third-party auditor must perform this audit. Matayo simplifies this process by offering automated SOC 2 Compliance Canada and expert guidance. This, in turn, helps businesses prepare for audits efficiently and ensures a smoother certification journey.
4. Undergo the SOC 2 Audit Process
Auditors verify if security controls match the expected standards by assessing deployed controls. A SOC 2 Type I certification evaluates system controls at a single point in time. However, a Type II certification tracks these controls throughout many months.
5. Access the SOC 2 Report and Maintain Certification
Once the audit is completed successfully, you’ll receive a SOC report. It helps verify compliance. However, you must ensure to maintain this certification. How? You must continuously monitor, periodically audit, and update security controls. These measures will effectively fight against the evolving threats and regulatory changes.

What are the Key Challenges in SOC 2 Certification and How Can You Overcome Them?
Getting a SOC 2 certification has many challenges. From resource constraints to maintaining long-term compliance, it had many loopholes. Nevertheless, with the right approach and support, businesses can easily overcome these obstacles. So, below we have given some of the common challenges and their respective solutions to ensure a smooth SOC 2 certification process.
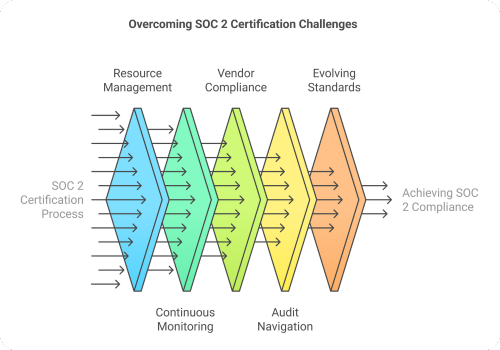
1. Managing Resource-Intensive Certification Needs
Businesses must examine their security controls before initiating SOC 2 Certification in Canada. A readiness assessment serves multiple purposes by discovering weak areas and assessing potential threats as well as determining which improvements are needed to fulfill Trust Services Criteria standards.
2. Ensuring Continuous Security Monitoring
Organizations need to create procedures together with policies along with technical protective measures because they need to match the SOC 2 standards. Secure operations require that businesses establish access controls together with data encryption features monitoring capabilities as well as incident management plans.
3. Addressing Third-Party Vendor Compliance
Always ensure a certified third-party auditor with specialized competencies in this field carries out the SOC audit. As a business owner, you should closely work with the firm while implementing your knowledge of industry-specific needs and assisting them through the audit procedure.
4. Navigating the Complexity of the Audit Process
Auditors verify if security controls match the expected standards by assessing deployed controls during aSOC audit. A SOC 2 Type I certification focuses on evaluating system controls at a single point in time. In contrast, Type II certification tracks these controls throughout multiple months to ensure their effectiveness over time.
5. Keeping Up with Evolving Security Standards
The organization attains SOC 2 report authorization to confirm compliance during a successful audit. The ongoing maintenance of security certification demands continuous oversight of security measures, scheduled audits, and security updates for adapting to ongoing threats and regulatory adjustments. Matayo helps businesses maintain long-term SOC 2 Compliance Canada by providing AI-driven monitoring and automated security updates. It further ensures they stay ahead of evolving regulatory requirements.
Conclusion
A SOC 2 Certification in Canada stands as essential for companies dealing with confidential customer information. This is so because it verifies their fulfilment of security, availability, and privacy standards. However, the process of achieving SOC 2 Compliance in Canada and its sustained maintenance, remains complex due to the need to track security standards changes and perform ongoing monitoring. Matayo helps businesses through its AI-powered solutions by providing automated security monitoring as well as audit preparation streamlining and continuous compliance maintenance services. Organizational efficiency in achieving certification and long-term security strength becomes possible through appropriate tools and expert support.


