UNDERSTANDING VAPT
In today’s digital landscape, businesses face an ever-growing array of cyber threats. Protecting data and maintaining the integrity of IT systems have become paramount.
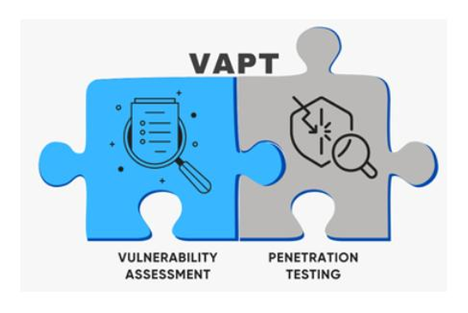
This is where Vulnerability Assessment and Penetration Testing(VAPT) come into play.
VAPT is a comprehensive approach to identifying, evaluating, and mitigating security vulnerabilities within an organization’s IT infrastructure. By understanding and implementing VAPT, businesses can proactively safeguard their assets against potential cyber attacks.
1.2 Importance of VAPT for Businesses
Vulnerability Assessment (VA) and Penetration Testing (PT) are distinct processes. A Vulnerability Assessment involves a thorough scan of an organization’s systems, networks, and applications to identify known vulnerabilities. This process is automated and helps in discovering weaknesses that could be exploited by attackers.

Penetration Testing, It involves simulating real-world attacks on the identified vulnerabilities to determine if they can be exploited. This manual process mimics the tactics, techniques, and procedures of actual cyber criminals, providing deeper insights into potential security breaches.
- VAPT helps in identifying security gaps before they can be exploited by malicious actors. This proactive approach enables businesses to patch vulnerabilities, thus reducing the risk of data breaches and cyber attacks.
- VAPT enhances the overall security posture of an organization by providing a clear understanding of the current security landscape. It empowers businesses to make informed decisions about their security strategies and investments.
Moreover, VAPT is crucial for regulatory compliance, such as GDPR, HIPAA, and PCI-DSS.
Regular VAPT assessments ensure that businesses comply with these regulations, avoiding hefty fines and legal repercussions. Additionally, demonstrating a commitment to robust cyber security practices can enhance a company’s reputation and build trust with customers, partners, and stakeholders.
1.3 Differences b/w Vulnerability Assessment and Penetration Testing
VAPT aim to improve an organization’s security, they differ in scope, methodology, and outcomes.
Scope: A Vulnerability Assessment is broad in scope, focusing on identifying vulnerabilities across the IT environment. It provides a comprehensive inventory of potential weaknesses. Penetration Testing, however, is more focused. It aims to exploit specific vulnerabilities to understand the extent and impact of a potential security breach.
Methodology: Vulnerability Assessment is typically automated, using various tools to scan systems for vulnerabilities. These tools generate a list of weaknesses, which can be prioritized for remediation.
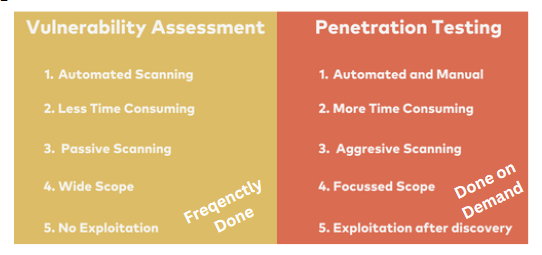
Penetration Testing involves manual testing techniques performed by skilled security professionals. It simulates real-world attacks to exploit vulnerabilities, providing a practical assessment of anorganization’s defenses.
THE RISING THREAT OF ATTACKS

2.3 The Imperative of Proactive Security
Given the emotional and tangible impacts of cyber attacks, proactive security measures are essential. VAPT offers a way to stay one step ahead of cyber criminals by identifying and mitigating vulnerabilities before they can be exploited. It empowers businesses to safeguard their digital assets, protect their reputation, and maintain the trust of their customers.
In the face of rising cyber threats, the question is not if a business will be targeted, but when. By embracing proactive security measures, businesses can transform fear and uncertainty into confidence and resilience. VAPT is not just a technical necessity—it is a commitment to protecting everything that your business stands.
UNDERSTANDING VAPT
Outcomes: The outcome of a Vulnerability Assessment is a detailed report that lists identified vulnerabilities, their severity, and recommendations for mitigation. This report serves as a roadmap for improving security. The outcome of Penetration Testing is a more in-depth analysis that includes not only identified vulnerabilities but also the potential impact of their exploitation. It provides actionable insights into how an attacker could gain access to critical systems and data.
In summary, By integrating VAPT into their security framework, businesses can achieve a higher level of resilience and confidence in their IT infrastructure.
THE RISING THREAT OF ATTACKS
In the digital age, the cyber attacks looms larger than ever. As we increasingly rely on technology to run our businesses, the threat of cyber attacks grows more imminent and daunting.
This chapter focus on impacts of cyber attacks on businesses, highlighting why proactive security measures like VAPT
2.1 The Emotional Toll of Cyber Attacks
Imagine to the news that your company’s data has been breached. Sensitive customer information, proprietary business data, and confidential communications are suddenly in the hands of malicious actors. The immediate reaction is panic, fear, and helplessness. For business owners and stakeholders, the emotional toll can be
devastating.
An unseen enemy has infiltrated your digital fortress. The trust you’ve built with your customers feels compromised, and the reputation. The anxiety of not knowing the full extent of the breach, coupled with the pressure to address the fallout swiftly and effectively, can be overwhelming.
2.2 The Rising Sophistication of Cyber Threats
As technology evolves, so too do the methods employed by cyber criminals. Today’s cyber attacks are increasingly sophisticated, often orchestrated by highly organized groups with vast resources at their disposal. These attackers continuously refine their techniques, making it harder for businesses to defend against them using traditional security measures.
Phishing schemes, ransomware attacks, and advanced persistent threats (APTs) are just a few examples of the sophisticated tactics employed by modern cyber criminals. These threats can bypass conventional security defenses, leaving businesses vulnerable to breaches. The evolving nature of cyber threats underscores the importance of staying ahead of the curve with advanced security measures like VAPT.

UNDERSTANDING VULNERABILITY ASSESMENT AND PENETRATION TESTING (VAPT)
In the world of cybersecurity, acronyms can often seem like a foreign language. Vulnerability Assessment and Penetration Testing (VAPT) are (2)two such critical concepts that, when properly understood and implemented, can provide a robust defense against potential breaches. In this chapter, we will dive into the emotional and practical aspects of VAPT, explaining why they are essential for your business’s ecurity and peace of mind.
Vulnerability Assessment is the process of systematically scanning your systems to identify potential weaknesses. It’s like a thorough health check-up for your IT environment, pinpointing areas that need attention.
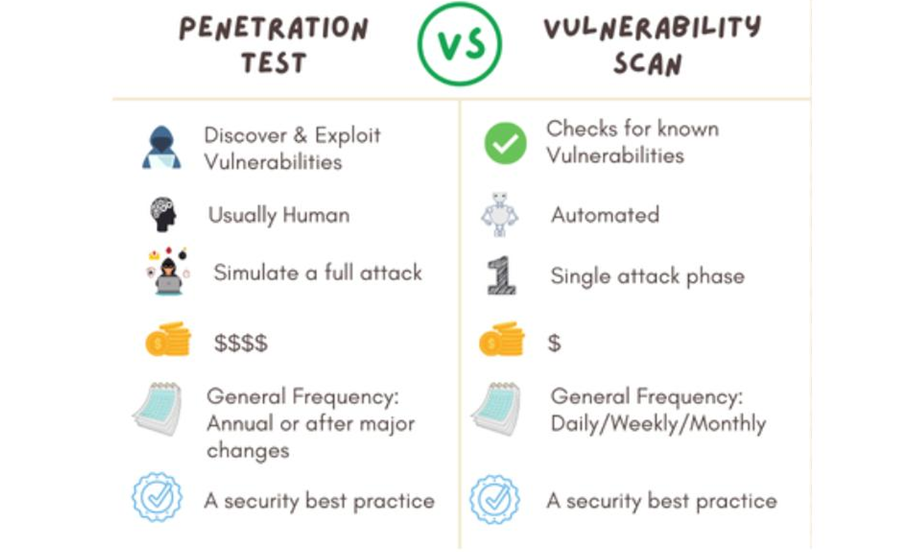
Penetration Testing, on the other hand, simulates real-world attacks to see how well your defenses hold up. It’s about stress-testing your systems to uncover how they might be exploited by malicious actors.
UNDERSTANDING VULNERABILITY ASSESSMENT AND PENETRATION TESTING (VAPT)
3.1 The Assurance of Knowing
Vulnerability Assessment provides a detailed map of potential risks, allowing you to address them proactively.
Penetration Testing goes a step further by actively challenging your defenses, revealing how your systems would stand up under real-world conditions.
The insights gained from these tests provide a clear action plan to bolster your defenses.
3.2 The Commitment to Security
Embracing VAPT is a commitment to ongoing security. It’s not a one-time effort but a continuous process of assessment, testing, and improvement. Cyber threats evolve, and so must your defenses.
Regular VAPT ensures that your security measures remain effective and up-to-date, adapting to new challenges as they arise.
PREPARING FOR VAPT
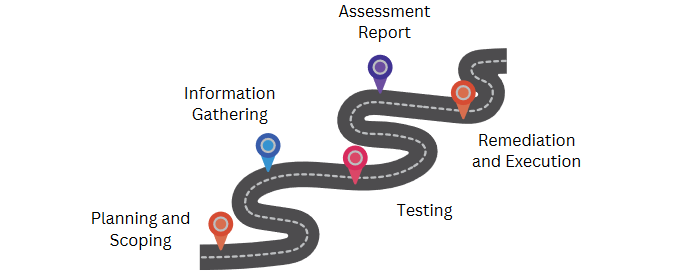
Preparing for a Vulnerability Assessment and Penetration Testing (VAPT) is a critical step that requires planning and coordination. This phase ensures that your organization is ready to identify and address potential security vulnerabilities effectively.
Understanding the Scope: Define the scope that involves identifying the systems, networks, applications, and data that will be tested. Clear boundaries must be set to avoid any unintended disruptions to business operations. Engage with key stakeholders to determine the assets and prioritize them for assessment.
Stakeholder Communication: Communication with IT teams, management, and any 3rd -party service providers. Inform them about the upcoming VAPT, its purpose, and the potential impact on operations. Establish a communication plan to keep everyone updated throughout the process.
Documentation and Inventory: Compile comprehensive documentation of your IT infrastructure. This includes network diagrams, system configurations, and application inventories.
Access and Permissions: Ensure necessary access and permissions to perform the testing. This might involve creating temporary accounts, providing VPN access, or configuring firewall rules. Proper access control measures should be in place to protect sensitive information during the assessment.
Backup and Contingency Plans: Ensure that all critical data is backed up. Develop contingency plans to address any potential disruptions caused by the testing. This includes having incident response protocols in place to quickly resolve any issues that may arise.
Define Success Metrics: Establish metrics and objectives for the VAPT. Determine what constitutes a successful assessment and how the findings will be addressed. This helps in measuring the effectiveness of the VAPT and provides a roadmap for remediation efforts.
PREPARING FOR VAPT
By thoroughly preparing for a VAPT, you set the stage for a successful assessment that can significantly enhance your organization’s security posture. This proactive approach not only identifies vulnerabilities but also fortifies your defenses against potential cyber threats.

