REMEDIATION STRATEGIES
Remediation strategies are the actionable steps your organization takes to address the vulnerabilities identified during the VAPT process. Effective remediation not only mitigates existing risks but also strengthens your overall security posture, reducing the likelihood of future threats.
7.1 Prioritizing Vulnerabilities: Prioritizing the vulnerabilities based on their severity and potential impact. High and critical vulnerabilities should be addressed immediately, as they pose the greatest risk. Medium and low vulnerabilities, while less urgent, should also be scheduled for remediation to ensure comprehensive security.
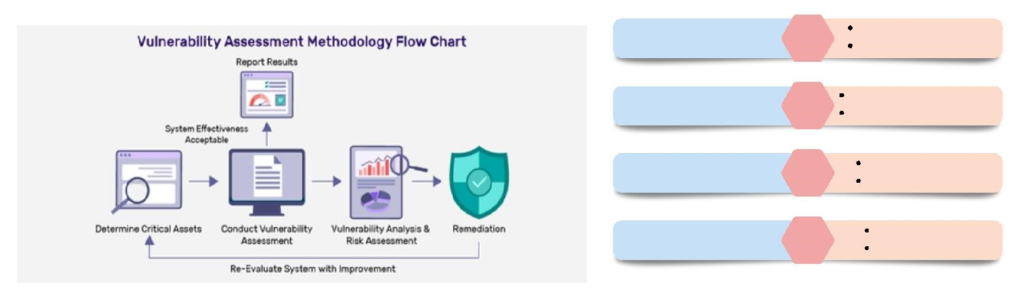
7.2 Enhancing Security Controls: Strengthen existing security controls this could include network segmentation, enhanced monitoring and logging, intrusion detection systems (IDS), and endpoint protection solutions. These controls add multiple layers of defense, making it harder for attackers to penetrate your systems.
7.3 User Training and Awareness: Human error is often a significant factor in security breaches. Conduct regular training sessions to educate employees about security best practices, phishing attacks, and safe internet usage. An informed workforce is a crucial component of a robust security strategy.
7.4 Regular Audits and Reassessments: Security is an ongoing process. Schedule regular audits and reassessments to ensure that remediation efforts are effective and that no new vulnerabilities have been introduced. Continuous monitoring and periodic VAPT assessments help maintain a strong security posture.
Implementing these remediation strategies systematically ensures that vulnerabilities are addressed effectively, reducing the overall risk to your organization. By prioritizing, patching, reconfiguring, enhancing controls, training users, and maintaining vigilant oversight, you can create a resilient security environment that safeguards your assets and data.

COMPLIANCE AND REGULATORY REQUIREMENTS
Navigating the complex landscape of compliance and regulatory requirements is a critical aspect of any organization’s security strategy. Ensuring compliance not only protects your business from legal penalties but also builds trust with clients and stakeholders. This chapter delves into the importance of meeting these requirements and how VAPT (Vulnerability Assessment and Penetration Testing) plays a pivotal role in achieving compliance.
8.1 Understanding Regulatory Frameworks: Regulatory frameworks that mandate specific security measures. Examples include the General Data Protection Regulation (GDPR) for data privacy in the European Union, the Health Insurance Portability and Accountability Act (HIPAA) for healthcare data in the United States, and the Payment Card Industry Data Security Standard (PCI DSS) for organizations handling credit card information. Familiarize yourself with the regulations applicable to your industry and geographical location to ensure comprehensive compliance.
8.2 Role of VAPT in Compliance: Many regulatory frameworks require regular security assessments to protect sensitive data. Conducting VAPT not only helps in uncovering potential security weaknesses but also demonstrates your commitment to maintaining a secure environment, which is often a compliance requirement.
8.3 Documentation and Reporting: Proper documentation is crucial for demonstrating compliance. Detailed reports generated from VAPT exercises provide evidence of your proactive efforts to identify and address security issues. These reports can be presented to auditors and regulatory bodies to showcase your adherence to mandated security practices.
8.4 Collaboration with Legal and Compliance Teams: Work closely with your legal and compliance teams to understand the specific requirements and deadlines for your industry. Their expertise will guide you in aligning your security practices with regulatory expectations, ensuring that all necessary measures are in place.
8.5 Benefits of Compliance: Beyond avoiding legal repercussions, compliance enhances your organization’s reputation. Clients and partners are more likely to trust and engage with a company that demonstrates a strong commitment to security and regulatory adherence.
In conclusion, achieving and maintaining compliance requires a thorough understanding of relevant regulations, regular security assessments like VAPT, and meticulous documentation. By integrating these practices into your security strategy, you can safeguard your organization against legal risks and build a foundation of trust and reliability with your stakeholders.

IMPORTANCE OF CONTINUOUS IMPROVEMENT & VIGILANCE
In the wake of a cyber attack, it’s easy to become complacent once the immediate threat has been mitigated. However, true resilience and security come from a commitment to continuous improvement and unwavering vigilance. This chapter delves into the emotional journey of embracing a culture of ongoing enhancement and the critical role it plays in protecting your organization from future threats.
9.1 The Emotional Toll of Complacency
Complacency can be one of the most dangerous mindsets in the realm of cybersecurity. After overcoming a significant challenge, it’s natural to feel a sense of relief and accomplishment. But this is precisely when your defenses are most vulnerable.
By investing in your people and prioritizing their role in cybersecurity, you are not just protecting your business; you are fostering a sense of community and shared responsibility.

9.2 Cultivating a Mindset of Continuous Improvement
Continuous improvement is not just a strategy; it’s a mindset. It requires a commitment to never settling for the status quo and always striving for better. This mindset should permeate every level of your organization, from the C-suite to the front lines.
Start by fostering an environment that encourages innovation and the pursuit of excellence. Celebrate small wins and incremental improvements, showing that every step forward, no matter how small, contributes to the overall security posture.
The future of cybersecurity is a landscape of endless possibilities, where innovation and proactive measures pave the way for stronger defenses. By embracing emerging technologies, committing to continuous learning, and fostering a proactive security culture, we can navigate the uncertainties of the future with confidence and resilience.
Together, we can build a future where cybersecurity is not just a necessity, but a shared mission that unites and empowers us all.
ABOUT THE AUTHOR

Mr. Sreenath Padmanabhan is a seasoned professional with over 25 years of experience in the fields of Process Improvement, IT Security and Governance. With a rich and diverse industry background, he has established himself as an expert in implementing a wide range of information security and compliance frameworks.
Sreenath’s extensive career has been marked by his dedication to helping organizations safeguard their information assets and achieve compliance with international standards.
His deep understanding of Complaince with Continuous Improvement Programs has enabled numerous businesses to enhance their security posture, mitigate risks, and ensure regulatory compliance.
As the author of this e-book, Sreenath brings his vast knowledge and practical experience to the forefront, providing invaluable insights and guidance for organizations.
His passion for information security and his dedication to continuous improvement are evident in every chapter, making this e-book an essential resource for professionals seeking to enhance
their security posture.
His work continues to inspire and guide organizations toward achieving their security and compliance goals, ensuring the protection of critical information assets in an increasingly complex digital landscape.

