HIPAA Compliance in Canada: How Healthcare Providers Are Upgrading from Data Privacy to Cyber Resilience
The healthcare professionals in Canada are experiencing a severe transformation regarding securing confidential patient data. Although data privacy laws, including PHIPA and PIPEDA, have traditionally influenced the data handling practice, increasing cyber threats are revealing the weakness of this compliance-based approach. Simultaneously, the HIPAA standards have a positive impact on the Canadian healthcare institutions operating cross-border data, with the use of U.S.-based technologies, or serving international patients. With rising ransomware attacks, system failures, and data breaches, healthcare providers are shifting beyond data protection to cyber resilience with a focus not only on preventing them but also on preparedness, response, and quick recovery to provide patients with uninterrupted care.

Why healthcare providers are focusing on Cyber resilience besides data privacy?
Going beyond the privacy of data and focusing on cyber resilience is the crucial step for healthcare providers because merely securing the patient data will no longer suffice to preserve healthcare operations. Conventional data privacy models are mainly concerned with unauthorized access prevention and regulatory compliance. Although of necessity, these measures fail to cover the present-day cyber threat environment, where attacks are becoming more advanced, prolific, and disruptive.
Ransomware and cyberattacks are two of the prevalent ways to attack healthcare organizations. A single cyber attack can cause the loss of clinical systems, emergency disruption, and patient safety. Cyber resilience enables healthcare providers to anticipate threats, withstand attacks, react, and recover promptly to minimize downtime in operations and clinical consequences.
Moreover, the healthcare environment has gone beyond the traditional network to incorporate electronic health records, telehealth, cloud computing, and integrated medical devices. This online ecosystem is growing, and it presents more cyber threats to users that cannot be addressed using privacy settings. Cyber resilience implements active surveillance, an incident response plan, system redundancy, and staff preparedness that enable the provision of care despite cyber-disruption.
Lastly, cyber resilience fills the gap between business continuity and patient safety or security by allowing healthcare providers to deliver reliable care, maintain trust, adhere to the rules, and ensure organizational stability.
Significance of HIPAA Compliance in Protecting Healthcare Data Privacy
Compliance with HIPAA is essential to ensure the privacy of healthcare data and improve the overall security stance of healthcare organizations. In addition to compliance with regulatory requirements, HIPAA provides a systematic framework that directly enhances patient safety, operational sustainability, and long-term trust.
● Patient safety
Keeping patient data safe is highly associated with keeping patient lives safe. The confidentiality, integrity, and availability of information on patient health are guaranteed by HIPAA safeguards. Once clinical systems and patient records are safe, the information accessed by the professionals is not disrupted. Breach of data or outage of the system may result in slow diagnosis, interfere with treatment, or cause medical errors. HIPAA assists in providing a reliable healthcare delivery and minimizes the risk to patient safety by establishing effective access controls, audit trails, and security protection.
● Regulatory compliance
HIPAA establishes good criteria in handling, storing, and transferring healthcare information. Compliance shows that an organization has followed internationally accepted standards of data protection. For healthcare providers operating outside the borders or using U.S.-based technologies, the case of HIPAA compliance will help to fulfill the contractual and legal needs and meet the Canadian privacy regulations, such as PHIPA and PIPEDA. Compliance will reduce the risks of investigations and litigation.
● Operational continuity
The measures that are considered in the Security Rule of HIPAA include the risk assessment, incident response planning, and contingency planning. The requirements will support organizations in the preparation for cyber incidents, the minimization of downtimes, and the speedy recovery. HIPAA compliance helps in continuity of care, during a cyberattack, technical breakdown, or data breach, since it protects system availability.
● Reputation management
Trust is the most important in the sphere of healthcare. Patients would prefer their medical confidential information to be treated in a safe and ethical way. A data breach will have a hard impact on the organizational image, which will lose the confidence of patients, and it will be featured in the media. Compliance with HIPAA is an indication of the dedication to the privacy of data and proper management in a responsible way, which allows healthcare organizations to gain credibility among patients, partners, and regulators.
● Financial management
The lack of compliance with HIPAA can be hefty financial penalties, legal repercussions, and remediation expenses. Breach of data also adds to the costs of operations in the form of recovery of the system, investigation, and lost business. The investment in HIPAA-compliant security assists healthcare organizations in reducing the extent of financial losses, fines, and long-term earnings and ensures sustainable development.
All these factors underscore the need for HIPAA compliance in the privacy of healthcare data, as well as the resilience and reliability of the healthcare systems.
Ways Healthcare Providers are enabling HIPAA Compliance to upgrade from Data Privacy to Cyber Resilience
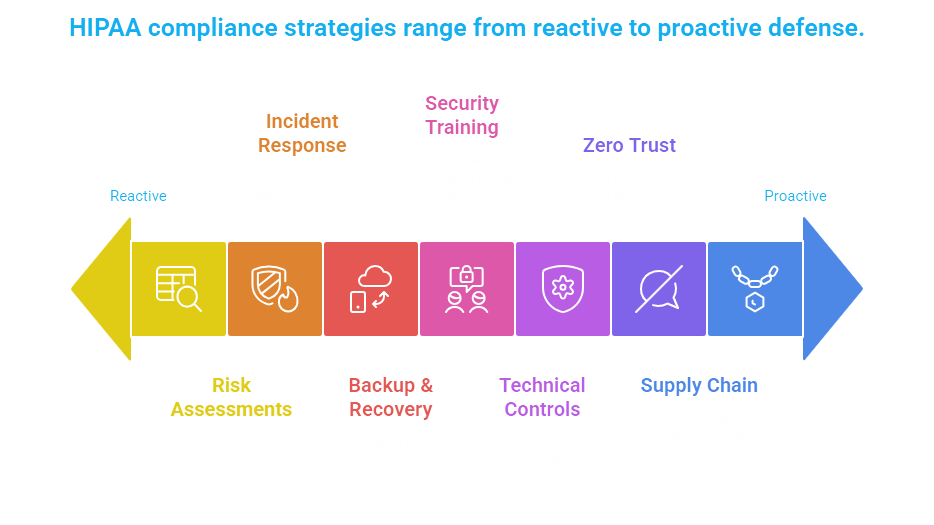
The healthcare providers are beginning to realize that being HIPAA compliant includes not only adhering to the data privacy requirements, but establishing cyber resiliency that guarantees continuity of care amidst the changing cyber threats. With the alignment of the HIPAA Security Rule requirements with the current cybersecurity strategies, organizations are turning compliance into a proactive defense model. These are the main ways healthcare providers are helping HIPAA compliance go beyond the basic data protection and become real cyber resilience.
● Risk Assessments and Gap Analyses
The concept of HIPAA compliance and cyber resilience is founded on the risk assessment. The medical practitioners conduct a periodical system evaluation through workflows and data landscapes to identify system weaknesses that can expose their shielded health information (PHI). Gap analyses are used to compare the existing security control measures with HIPAA security rule requirements and indicate weaknesses in access regulations, encryption, monitoring, or personnel practices. By conducting a continuous risk reevaluation, especially after the upgrade of the system, post-cloud migration, or installation of medical equipment, organizations will be able to prioritize remediation efforts and reduce the risk of data breach or downtime.
● Zero Trust Architecture
Zero Trust architecture is now a task force that healthcare organizations are adopting to enhance the security of PHI. Zero Trust does not assume that there will be any trust in the network, but instead continuously verifies the users, devices, and applications. When a cyber incident occurs, healthcare providers use the least-privilege access and strong authentication of identities and network segmentation to make sure that there is limited lateral movement. This will not only be in line with the provisions of access control stipulated by HIPAA but also significantly reduce the impact of a stolen credential or insider attacks.
● Incident Response Planning
The HIPAA compliance is concerned with preparedness, and incident response planning remains one of the primary features of cyber resilience. Incident response plans are written and developed by the healthcare providers, and they include details of the roles, obligations, communication procedures, and escalation channels of the security incident. Tabletop exercises and simulations that are conducted on a regular basis help the staff to simulate real-life scenarios such as ransomware attacks or data breaches. Having an efficient incident response plan, which is tested, can contain it sooner, cut down on downtime, and ensure that the notification requirement of a breach is achieved.
● Backup and Disaster Recovery
The availability of data is as crucial as the confidentiality of data in healthcare. HIPAA-compliant backup and disaster recovery solutions emphasize securing patient information and fast recovery of the system. Medical professionals use encrypted and irrevocable offline or resilient cloud backups. Frequent recovery testing allows the data to be recovered in a short time without the loss of integrity. These controls will ensure organizations are not attacked by ransomware, their hardware fails, or due to natural disasters, there is a continuity of care for the patients.
● Security Awareness and Training
Human error is also one of the major causes of healthcare data breaches. To counter this, health workers invest in continuous security awareness and training programs according to the HIPAA specifications. The phishing threats, password management, device management, and data management procedures are taught to employees. Routine training, simulations, and policy refreshers will create a culture of security consciousness among the staff members who will engage in the activity of safeguarding PHI and notifying about suspicious actions.
● Technical Controls
The HIPAA compliance and cyber resilience are built on the technical safeguards. Some of the tools deployed by healthcare providers include encryption of data at rest and data in transit, multi-factor authentication, endpoint detection and response (EDR), and nonstop monitoring. Logging and audit trails allow an organization to see what is going on in the system and then act on any anomalies promptly. Such technical controls will not only secure sensitive data, but they will also assist in the quick detection of threats and forensic analysis.
● Third-Party and Supply Chain Security
The healthcare ecosystems are extremely dependent on third-party vendors, cloud services, and service partners. The HIPAA compliance also requires healthcare providers to make sure that business partners have the necessary security controls. Organizations perform vendor risk assessment, implement the security requirements of contracts, and oversee the adherence to the third-party on a continuous basis. Healthcare providers decrease the exposure to external risk and guard PHI across systems linked together by enhancing supply chain security.
Rapidly combining HIPAA compliance with the current cybersecurity policies, healthcare providers can no longer afford to implement security methods of a reactive and privacy-centered nature, but instead adopt a robust security position. Such actions will not only secure patient information but will also provide continuity of operations, patient safety, and sustained confidence in a healthcare system that is gradually becoming more digital.

Conclusion
In the modern threat environment, healthcare providers should not just be concerned with the simplest data protection, but they should develop actual cyber resiliency. Organizations can safeguard patient data and guarantee continuity of care by incorporating HIPAA-consistent risk evaluations, Zero Trust, incident preparation, backups, training, technological preventions, and third-party monitoring. Cyber resilience enhances credibility, protection, and business continuity within a networked medical setting. To implement the most sophisticated AI-based solutions to assist with compliance and security automation, network with our cyber specialists at Matayo, and we will offer solutions that help your healthcare organization remain resilient and ahead of the future.

