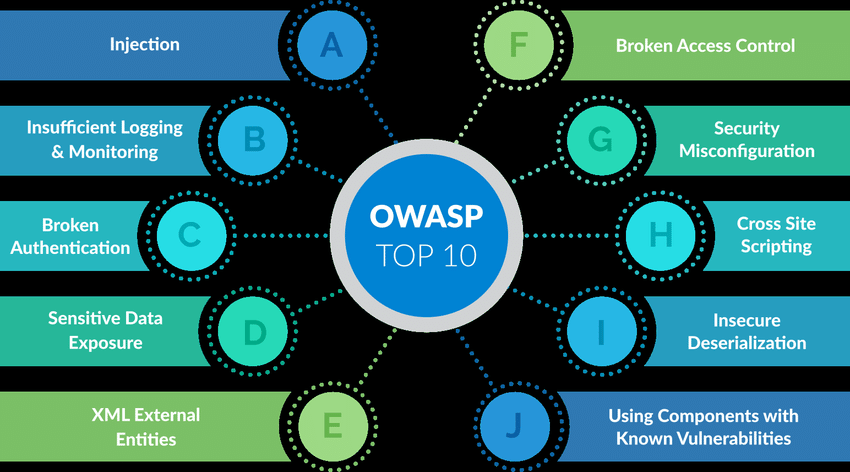
Web Application VAPT Services
Secure your web applications with our VAPT services. We identify vulnerabilities, assess risks, and deliver solutions to enhance your web application's security and protect against cyber threats.

Protect Your Web Applications with VAPT Solutions
We conduct detailed assessments to uncover weaknesses, followed by rigorous penetration testing to simulate real-world attacks. This dual approach not only highlights existing security gaps but also provides actionable insights to strengthen your defenses. By leveraging our VAPT solutions, you can safeguard sensitive data, maintain customer trust, and ensure compliance with industry standards.